Previous system design: here
Implementation Steps and Architecture Design
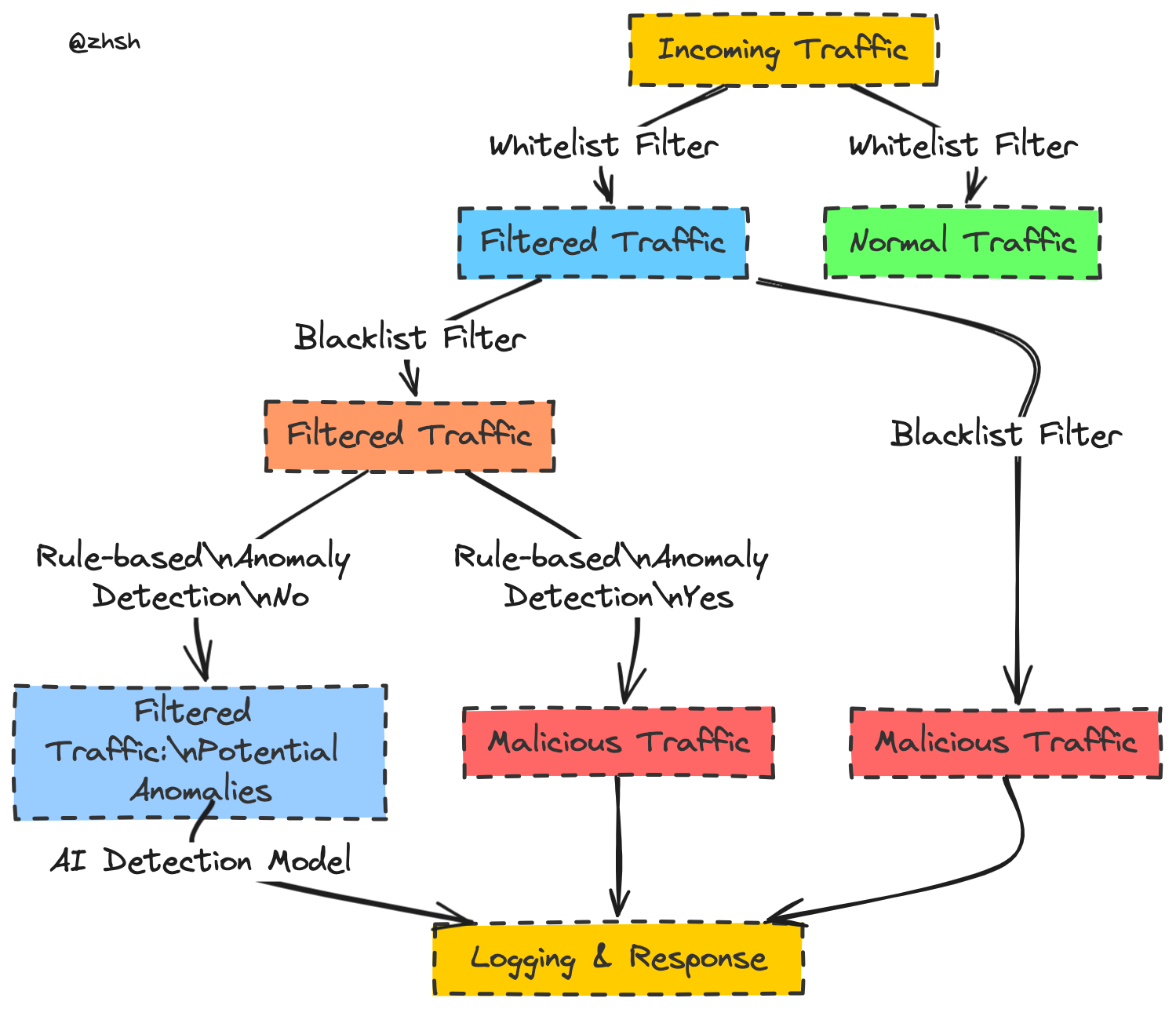
1. Whitelist Filtering
- Continue using existing whitelist rules to quickly filter normal traffic, reducing the load on subsequent modules.
2. Blacklist Filtering
- Further filter the traffic that passed the whitelist using blacklist rules to block known malicious traffic. This can be based on IP addresses, URL patterns, known malicious payloads, etc.
3. Anomaly Detection Module
- Perform anomaly detection on traffic that passed the blacklist. Anomaly detection can capture unknown attack patterns or abnormal behavior. Consider using:
- Statistical Anomaly Detection: Detect anomalies based on traffic statistical features (e.g., request frequency, response time).
- Signature-Based Detection (e.g., Snort): Use a tool like Snort to perform signature-based detection. Snort can analyze network traffic and compare it against a database of known attack signatures to identify potential threats.
4. ML&DL Detection Model
- Machine Learning Anomaly Detection: Use unsupervised learning algorithms (e.g., Isolation Forest, One-Class SVM) to detect anomalous traffic patterns.
- Feed the traffic that passed the whitelist, blacklist, and anomaly detection into the AI model for in-depth detection. The AI model can be based on deep learning, specifically designed to detect complex attack patterns (e.g., SQL injection, XSS).
5. Logging and Response
- Log all detection results and take appropriate response actions based on the detection results (e.g., block requests, send alerts).
Implementation Details
Whitelist and Blacklist Rules Management
- Define and maintain whitelist and blacklist rules. Use configuration files or databases to store rules and provide interfaces for easy updates.
Anomaly Detection Module
- Select appropriate anomaly detection algorithms and train and tune them. Use historical traffic data for training to ensure the model accurately captures abnormal behavior.
AI Detection Model
- Train the AI model using labeled data to ensure it can recognize various complex attacks. Regularly update the model to address new attack patterns.
Performance Optimization
- Optimize each module to ensure efficient operation under high traffic conditions. Use parallel processing, caching mechanisms, etc., to improve performance.
System Testing
- Conduct comprehensive testing of the entire system to ensure all modules work together and accurately detect and respond to various attacks.