Integrated Real-time HTTP Intrusion Detection System: Simulation System Design
In the pursuit of advancing the capabilities of an Integrated Real-time HTTP Intrusion Detection System (IDS), the critical need for extensive and diverse datasets cannot be overstated. Given the paucity of available data sources, the creation of a simulation system to automatically deploy varied HTTP servers (targets) and generate both benign and Proof of Concept (PoC) malicious traffic becomes imperative. This document outlines the design and functionality of such a simulation system.
System Description
The proposed simulation system aims to emulate a realistic network environment where multiple HTTP servers are deployed as targets. The system will orchestrate the generation of normal traffic and PoC malicious traffic to these servers, subsequently collecting HTTP log data for analysis and benchmarking.
System Features
- Automated Deployment of HTTP Servers:
- The system will dynamically provision multiple HTTP servers, each configured with varying parameters to mimic real-world diversity.
- Servers will be instantiated using container orchestration tools such as Docker and Kubernetes, ensuring scalability and manageability.
- Traffic Generation:
- Normal Traffic: Utilizes pre-defined user behavior patterns to generate legitimate HTTP requests, simulating typical user interactions.
- Malicious Traffic: Generates PoC attacks based on known vulnerabilities and exploits, simulating scenarios of potential security breaches.
- Data Collection and Logging:
- All HTTP traffic, both benign and malicious, will be meticulously logged.
- Logs will be stored in a centralized database for subsequent analysis, allowing for the extraction of meaningful insights and the development of robust detection algorithms.
System Workflow
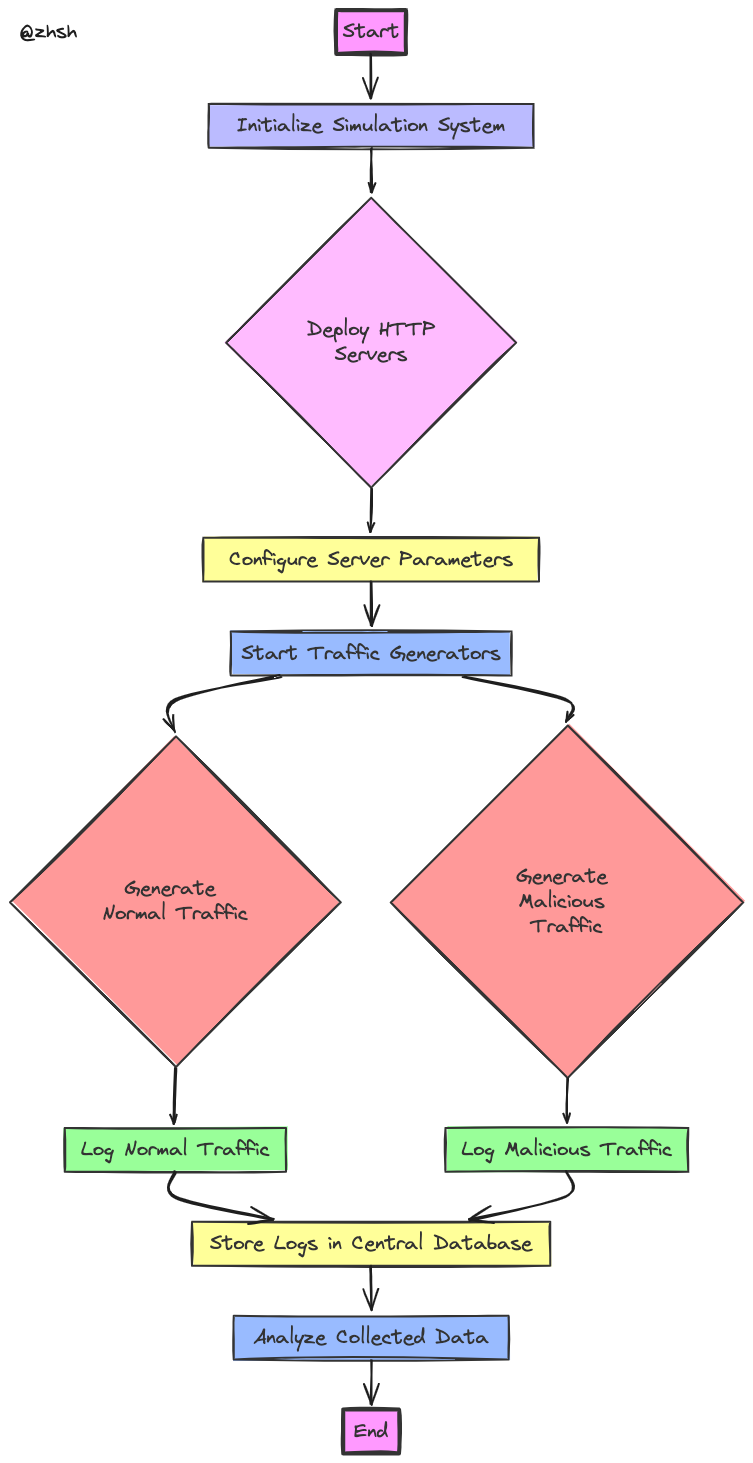
- Start: The simulation process initiates.
- Initialize Simulation System: The system is configured and prepared for deployment.
- Deploy HTTP Servers: Multiple HTTP servers are deployed using container orchestration tools.
- Configure Server Parameters: Each server is configured with specific parameters to emulate different real-world scenarios.
- Start Traffic Generators: Traffic generators are activated.
- Generate Normal Traffic: Normal traffic is generated based on predefined user behavior patterns.
- Log Normal Traffic: Normal traffic is logged for analysis.
- Generate Malicious Traffic: PoC malicious traffic is generated to simulate attacks.
- Log Malicious Traffic: Malicious traffic is logged.
- Store Logs in Central Database: All logs are stored in a centralized database.
- Analyze Collected Data: Collected data is analyzed to extract insights and improve detection algorithms.
- End: The simulation process concludes.
Conclusion
This simulation system represents a crucial step towards the development of a more robust and effective HTTP Intrusion Detection System. By automating the deployment of diverse HTTP servers and generating a comprehensive dataset of both normal and malicious traffic, this system will provide the necessary foundation for training advanced machine learning models and benchmarking rule-based algorithms. Through meticulous design and implementation, this simulation system will significantly enhance the capability to detect and mitigate HTTP-based intrusions in real time.
When building a simulation system to deploy various HTTP servers as targets, choosing appropriate open-source projects is crucial. Below are some widely-used open-source target projects suitable for simulation testing and security research:
-
DVWA (Damn Vulnerable Web Application):
- Description: A very vulnerable PHP/MySQL web application designed to help security professionals test their skills and practice common web vulnerabilities.
- Link: DVWA
-
OWASP Juice Shop:
- Description: A modern, fully functional JavaScript web application that contains vulnerabilities ranging from easy to complex. It is an OWASP project and is excellent for practical security testing.
- Link: OWASP Juice Shop
-
WebGoat:
- Description: A teaching-oriented web application maintained by OWASP, designed to teach web application security lessons. It contains multiple vulnerabilities for users to learn and practice.
- Link: WebGoat
-
Mutillidae:
- Description: An open-source, easy-to-install web application that contains a large number of configurable vulnerabilities. It is designed for security testing and education.
- Link: Mutillidae
-
bWAPP (Buggy Web Application):
- Description: A vulnerable web application designed to help security enthusiasts discover, learn, and prevent web vulnerabilities. It includes over 100 different vulnerabilities.
- Link: bWAPP
-
Vulnerable Node:
- Description: A vulnerable web application based on Node.js, designed to provide a platform to learn and test Node.js-specific security vulnerabilities.
- Link: Vulnerable Node
-
Hackazon:
- Description: A simulated e-commerce website that contains multiple security vulnerabilities for users to learn and practice web application security.
- Link: Hackazon
-
WackoPicko:
- Description: A vulnerable web application designed for security testing and education. It simulates a photo-sharing website with various common web vulnerabilities.
- Link: WackoPicko
These open-source projects can be integrated into your simulation system using automation scripts and containerized deployment to quickly start and stop them.